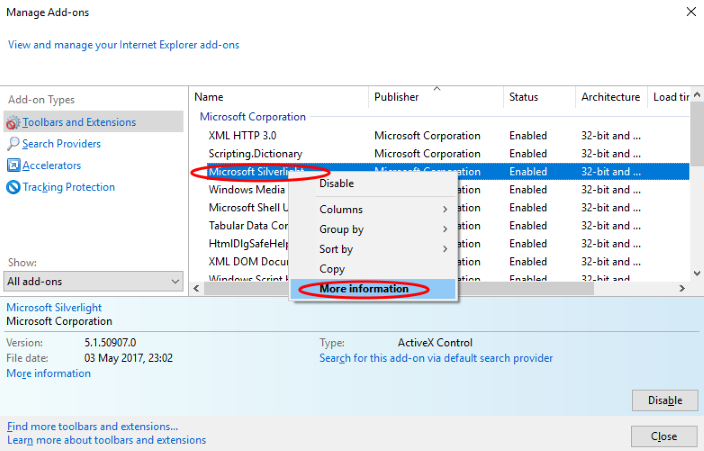
Microsoft Silverlight is a component in many web browsers that helps them stream and display video, music, clickable menus, and other types of 'rich media' content. Launched in 2007, it was.
- RECOMMENDED: Use Silverlight in the 32-bit Internet Explorer process on x64 systems. Most browser plug-ins (including Silverlight, Flash, Java and almost all ActiveX controls) only work in 32-bit browsers currently.
- Microsoft Silverlight (or to simplify Silverlight) is a deprecated application framework designed for writing and running rich web applications, similar to Adobe's own runtime, Adobe Flash. A plugin for Silverlight is still available for a very small number of browsers.
- Microsoft Silverlight is a powerful tool for creating and delivering rich Internet applications and media experiences on the Web. Silverlight 5 builds on the foundation of Silverlight 4 for building business applications and premium media experiences.
Ms Silverlight Msi
MS-ISAC ADVISORY NUMBER:
 2016-135
2016-135Ms Silverlight Uses
DATE(S) ISSUED:
09/13/2016
OVERVIEW:
A vulnerability has been discovered in Microsoft Silverlight, which could allow for remote code execution. Microsoft Silverlight is a media application for browsers on Microsoft Windows and Apple Mac OS technologies. Successful exploitation of this vulnerability could result in an attacker gaining the same privileges as the logged on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
THREAT INTELLIGENCE:
There are currently no reports of these vulnerabilities being exploited in the wild.
SYSTEMS AFFECTED:
- Microsoft Silverlight 5 prior to version 5.1.50709.0
- Microsoft Silverlight 5 Developer Runtime prior to version 5.1.50709.0
RISK:
Government:
- Large and medium government entities: HIGH
- Small government entities: MEDIUM
Businesses:
- Large and medium business entities: HIGH
- Small business entities: MEDIUM
Home Users:
LOWTECHNICAL SUMMARY:
One vulnerability has been discovered in Microsoft Silverlight, which could allow for remote code execution (CVE-2016-3367). This vulnerability exists when Microsoft Silverlight improperly allows applications to access objects in memory. To exploit the vulnerability, an attacker could host a website that contains a specially crafted Silverlight application and then convince a user to visit the compromised website, typically by enticing them to click a link in an email or instant message.
Successful exploitation could result in an attacker gaining the same privileges as the logged on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
RECOMMENDATIONS:
We recommend the following actions be taken:

Apply appropriate patches provided by Microsoft to vulnerable systems immediately after appropriate testing.
Run all software as a non-privileged user (one without administrative privileges) to diminish the effects of a successful attack.
Remind users not to visit un-trusted websites or follow links provided by unknown or un-trusted sources.
Inform and educate users regarding the threats posed by hypertext links contained in emails or attachments especially from un-trusted sources.
REFERENCES:
Microsoft:
https://technet.microsoft.com/en-us/library/security/ms16-109.aspxCVE:
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3367Information Hub : Advisories